He recently got his driver’s license, but he already has hundreds of cars; David Colombo opened the Teslas from Bavaria to the whole world, let them honk and wink. So far Harsh He tells how he overtook the vehicles.
“Try blowing the horn if you want.” it sound. “Can you confirm that it worked?” The astonished Irishman confirms. David Colombo of Dinkelsbahl in Franconia has stunned a neighborhood somewhere in Ireland. And that without knowing the Tesla owner personally or ever seeing his Tesla Model X.
What happened? “It was an accidental discovery when I was looking for vulnerabilities on a customer’s system,” explains Colombo, an IT specialist. own security companyMILF in conversation with Harsh, “There I found an example of Tesla software that initially only told me the location of one vehicle, which was unusual. Since then I’ve wanted to know more and suddenly I had multiple vehicles under control.”
A vulnerability in third-party Tesla software enabled them to gain access to more than 25 Teslas in 13 different countries. The 19-year-old had access to the camera system, door locks, windows, horns and other vital functions of the vehicles. They even had the movement data available with them. “Theoretically, I would have gotten up to 30 vehicles in China as well, but I wasn’t interested in messing with China’s strict cybersecurity law, so I ignored those vehicles,” Colombo explains.
Shocked by the message, several Tesla drivers went looking for the problem, as Colombo had promised the developer of the faulty software that it would not be left vulnerable. It came to light only after the problem was resolved: it was an updated version of “Meanwhile”.Teslamate“, whose users did not have sufficiently secure access.
“TeslaMate” is a freely available data logger that collects vehicle information and processes it graphically. Users themselves place it on the server and then attach their vehicle to it. Once set up, you have access to trip and charging reports, consumption, various statistics, addresses visited and a logbook. Of course, access for unauthorized guests is not part of the plan and the equipment is not on a server freely available on the Internet.
After all, no control of the cars is possible
After Colombo looked at the source code for “Teslamate” and it was understood that the software neither separately stored nor encrypted access to the vehicle concerned, he adopted the Simple Standard for Graphical User Interface (“Grafana”). Access succeeded in taking over Tesla by entering the data. , He adds that access data, if necessary, is no barrier.
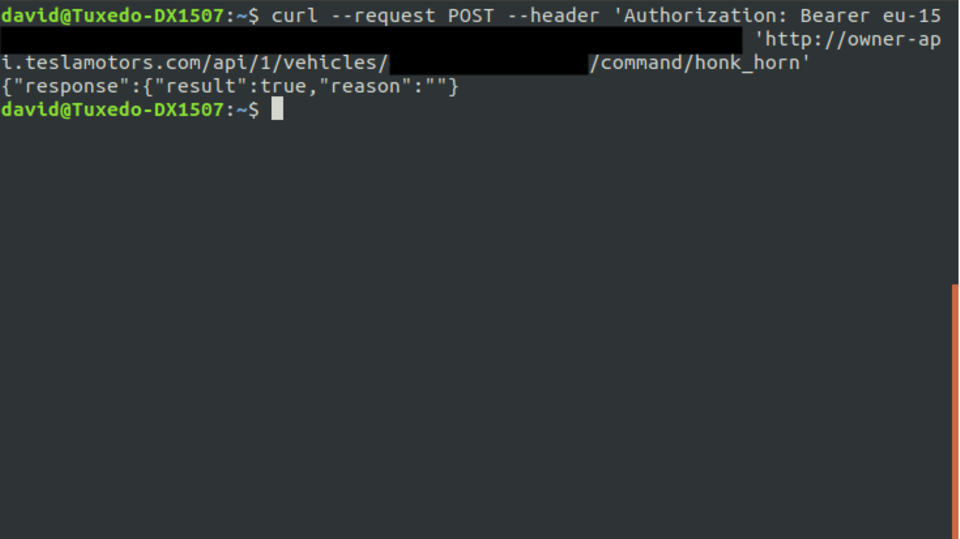
A little too complicated to warn road users quickly, but this is what it looks like when you horn a Tesla from Bavaria in Ireland.
© David Colombo
Only Colombo could not drive a car. But if these had the so-called “summoning” feature, he doesn’t want to rule out that he could move cars. With “Samon”, Tesla owners in the USA can drive their cars up to 150 meters in parking spaces without wheels, so they don’t have to walk all the way to the car. Significantly stricter limits apply to German drivers.
Tesla was publicly available on the Internet
Tesla is a highly digitized vehicle. If cars have reception, they can always access the network and send data. This is a connected tool such as “TeslaMate” or “fastlab“, which depends on the vehicles’ data streams. And for Colombo, this meant that vehicles with insufficient technical protection were virtually on its feet. Colombo shared very precise instructions on how to reach the cars Harsh, However, he wants to go public with all the details only when all possible targets for such an attack are certain.
Much more interesting than the exact process, which can no longer be done anyway due to the quick reactions of the developers concerned, are the possibilities that have opened up for Colombo. Because if he had acted in bad faith, it would have been a matter of a few clicks and input to turn on the Tesla flash and mid-drive. Of course, this is irritating to freeway occupants and other road users alike and is therefore potentially dangerous.
Tesla was informed and acted upon
The search puzzled Colombo: “It was frustrating. I had access to strangers’ cars, but there was no way to contact them. Through a thorough search, I was able to identify a handful of affected Tesla drivers and fix the error.” Was able to help them fix it, but ultimately I needed the manufacturer’s security team to reach everyone. All affected owners should have received a message by now.”

Eventually, he explains, he also had access to several hundred cars, but did not test their access at Tesla’s request. Meanwhile, the carmaker, with whom Colombo had worked closely from the beginning, recognized the problem, took early measures and blocked access. The developer of “TeslaMate” also modified its software and fixed the leak long before the report was published.
“I don’t blame anyone for this incident, neither Tesla nor the truly dedicated developer of the device,” Colombo says, “but I strongly advise against posting important things openly on the web. And urge every Tesla driver to be careful. Login. I discussed change requests for tools with developers and most of them have already been implemented. I also made some wishes for Tesla, but in general I Their security system seems to be solid.”
Harsh Also contact Tesla based on this story. Unfortunately, at the time of publication, it was unclear how the US automaker would look at, handle and resolve the matter, as no response had been received.

Reader. Organizer. General creator. Zombie fanatic. Alcohol advocate. Food junkie. Bacon ninja.





